Login Failed for User Domain Computername$ Powershell Updated FREE
Login Failed for User Domain Computername$ Powershell
In that location are several dissimilar tools to go information nearly the time of a user logon to an Active Directory domain. The fourth dimension of the final successful user authentication in an AD domain may exist obtained from the user lastLogon attribute it is just updated on the domain controller on which the user is authenticated) or lastLogonTimpestamp aspect (information technology is replicated between the DCs in a domain, simply only in 14 days by default). You can check the value of the user attribute using the AD attribute editor or with the Get-ADUser PowerShell cmdlet. Even so, sometimes you may want to view the history of user activity (logons) in a domain for a long catamenia of fourth dimension.
You can go information about successful user logon (hallmark) events from the domain controller logs. In this article we volition prove how to track user logon history in the domain using PowerShell. This manner you lot can get a consummate history of user activity in the domain, the fourth dimension when a user starts working and logon computers.
Contents:
- Agile Directory User Logon Inspect Policy
- Getting User Last Logon History with PowerShell
- Get Domain User Logon History Based on Kerberos Events
Active Directory User Logon Audit Policy
In order the information about successful/failed logon to exist collected in the domain controller logs, enable the audit policy of user logon events.
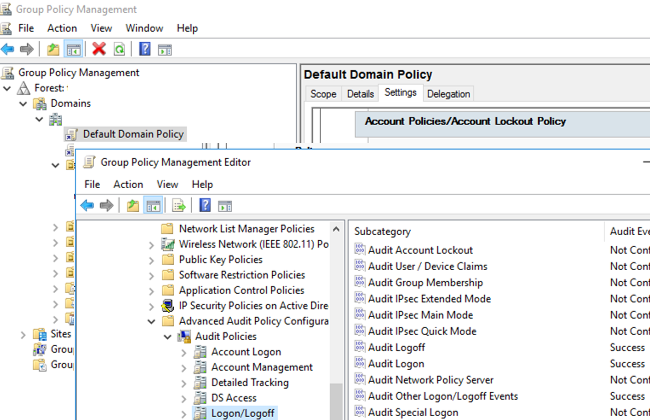
- Open the domain GPO management console (
GPMC.msc); - Open the Default Domain Policy GPO settings and go to Computer Configuration -> Policies -> Windows Settings -> Security Settings –> Avant-garde Audit Policy Configuration -> Audit Policies -> Logon/Logoff;
- Enable two audit policies (Inspect Logon andInspect Other Logon/Logoff Events). Select Success and Failure options in the inspect policy settings to register both successful and failed logons in the Security log on the DCs and computers;
- Save the changes in GPO and update the policy settings on your domain controllers using the following command: gpupdate /forcefulness (or expect for 90 minutes, DC replication time is not taken into account).
When a user logons to any computer in Agile Directory domain, an event with the Event ID 4624 (An account was successfully logged on) appears in the log of the domain controller that has authenticated the user (Logon Server). A successfully authenticated account (Account name), a calculator name (Workstation proper name) or an IP accost (Source Network Address) of a estimator used to logon are shown in the event description.
Also, you demand to check the value of the Logon Blazon field. We are interested in the post-obit codes:
- Logon Blazon 10 – Remote Interactive logon – a logon using RDP, shadow connexion or Remote Assistance (this event may appear on a domain controller if an administrator or non-admin user having RDP admission permission on DC logs on). This consequence is used to monitor and clarify the activity of Remote Desktop Services users.
- Logon Type 3 – Network logon (used when a user is authenticated on a DC and connects to a shared folder, printer or IIS service)
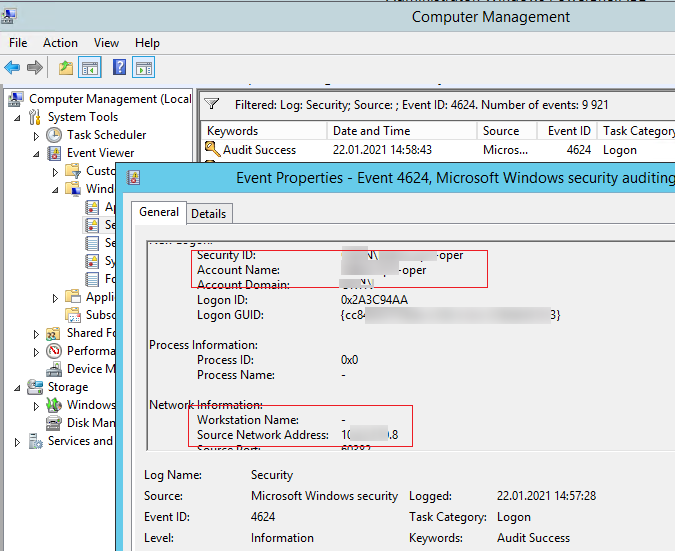
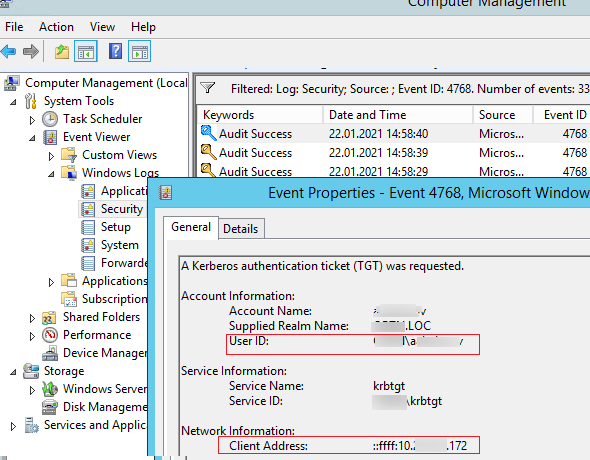
As well yous can runway a Kerberos ticket issue effect when authenticating a user. The Outcome ID 4768 is A Kerberos authentication ticket (TGT) was requested. To do it, enable the effect audit in the policy Account Logon –> Audit Kerberos Authentication Service -> Success and Failure.
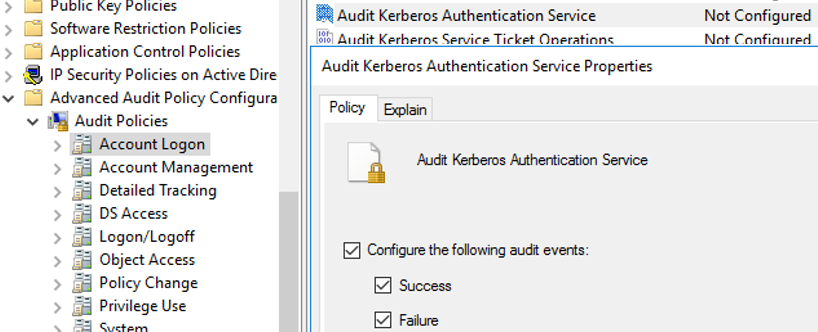
The outcome 4768 besides contains a name (IP accost) of a reckoner and a user account (Account Name or User ID) that received a Kerberos ticket (has been authenticated).
Getting User Last Logon History with PowerShell
Yous can use the Get-Eventlog PowerShell cmdlet to get all events from the domain controller'due south event logs, filter them by the EventID you want, and brandish information about the time when a user authenticated in the domain and a computer used to logon. Since there may exist multiple domain controllers in your domain and you may want to become a user logon history from each of them, use the Get-ADDomainController cmdlet (from the Advertisement module for Windows PowerShell). The cmdlet allows to get the list of all DCs in your domain.
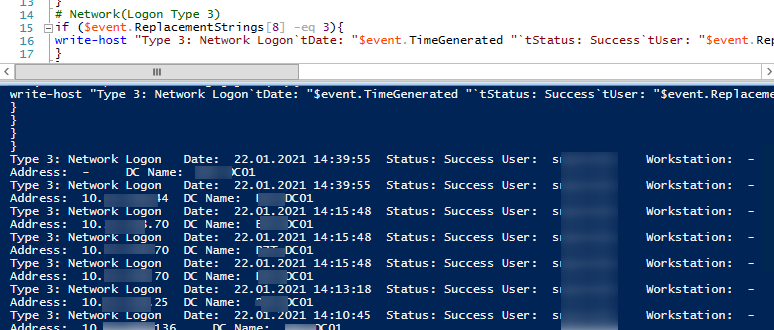
The post-obit PowerShell script allows yous to become all logon events for a user to an AD domain from all domain controllers. As a consequence, you volition get a table with the user logon history and computers a user authenticated from.
# a username, whose logon history you desire to view
$checkuser='*jbrown*'
# getting information about the user logon history for the last two days (you lot can modify this value)
$startDate = (become-engagement).AddDays(-2)
$DCs = Get-ADDomainController -Filter *
foreach ($DC in $DCs){
$logonevents = Get-Eventlog -LogName Security -InstanceID 4624 -later on $startDate -ComputerName $dc.HostName
foreach ($result in $logonevents){
if (($event.ReplacementStrings[v] -notlike '*$') -and ($issue.ReplacementStrings[five] -like $checkuser)) {
# Remote (Logon Type 10)
if ($outcome.ReplacementStrings[8] -eq 10){
write-host "Type 10: Remote Logon`tDate: "$event.TimeGenerated "`tStatus: Success`tUser: "$event.ReplacementStrings[5] "`tWorkstation: "$event.ReplacementStrings[11] "`tIP Accost: "$event.ReplacementStrings[18] "`tDC Proper name: " $dc.Name
}
# Network(Logon Type iii)
if ($result.ReplacementStrings[8] -eq 3){
write-host "Type iii: Network Logon`tDate: "$event.TimeGenerated "`tStatus: Success`tUser: "$event.ReplacementStrings[v] "`tWorkstation: "$event.ReplacementStrings[11] "`tIP Address: "$event.ReplacementStrings[18] "`tDC Name: " $dc.Proper name
}
}
}
}
Get Domain User Logon History Based on Kerberos Events
You can too get a user authentication history in the domain based on the result of a Kerberos ticket consequence (TGT Request — EventID 4768). In this case, less events volition be displayed in the output (network logons are excluded, equally well as admission events to the DC folders during getting GPO files or running logon scripts). The following PowerShell script will display the information most all user logons for the last 24 hours:
$alluserhistory = @()
$startDate = (go-date).AddDays(-1)
$DCs = Get-ADDomainController -Filter *
foreach ($DC in $DCs){
$logonevents = Get-Eventlog -LogName Security -InstanceID 4768 -afterwards $startDate -ComputerName $dc.HostName
foreach ($outcome in $logonevents){
if ($event.ReplacementStrings[0] -notlike '*$') {
$userhistory = New-Object PSObject -Property @{
UserName = $upshot.ReplacementStrings[0]
IPAddress = $event.ReplacementStrings[nine]
Engagement = $event.TimeGenerated
DC = $dc.Name
}
$alluserhistory += $userhistory
}
}
}
$alluserhistory
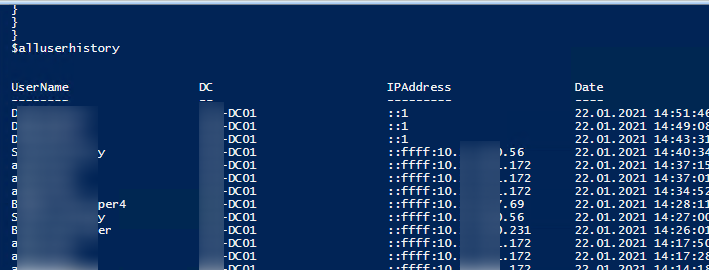
Notation that in this instance you won't run into any logon events of the users authenticated from clients or apps that use NTLM instead of Kerberos.
Login Failed for User Domain Computername$ Powershell
DOWNLOAD HERE
Source: http://woshub.com/check-user-logon-history-active-directory-domain-powershell/
Posted by: carlsontreff1938.blogspot.com
Comments
Post a Comment